Scenario-Based Training: Creating a Hands-On Course for Network & Security Operators
11:21:2019
Over the past year and a half, we have created content and held training events for Network and Security Operators. We call our events “Scenario-Based Training” because we provide the participants with situations related to a security or network incident. We have found that feedback for this type of training tends to be much more positive than vendor/product specific training because participants are able to use all the tools at their disposal and understand how to work in their own network better.
What is Scenario-Based Training?
Instead of learning how to use individual products, participants gain experience on how their own suite of network and security tools. Our teams that support the training include an instructor and various engineers (network, systems, and/or security). The engineers are referred to as the white cell (Department of Defense term), where our purpose is to generate traffic or other stimulus so that realistic traffic and incidents are being created. Operators working with network security tools can learn how to respond to these real world events. For example, we may simulate an attacker compromising hosts on their network, a user in distress that can’t access services, or a supervisor requesting an Intrusion Prevent System (IPS) signature to be made. While running these training events, our team has also learned a lot! This blog will talk a little bit about what we did, what went well, and what went wrong (and how we fixed it).
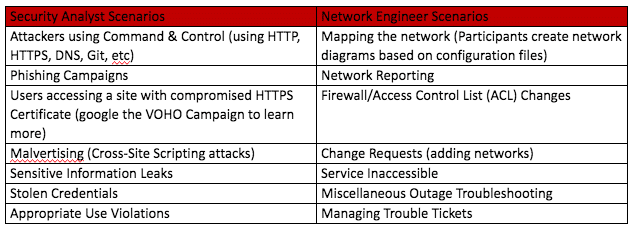
Cyber Security Scenario Options
In the training events that we have supported, we have delivered two different courses. One for security analysts that are responsible for maintaining security devices and monitoring the network. The other for network engineers that are responsible for pushing packets and making sure that the network is operational. During most of these scenarios, we as the white cell are responsible for running attacks, creating traffic, or making requests to kick off the scenario. After students take the necessary actions, we test what they did by re-running the events. Below are some examples of what the scenarios that we have run for students.
After teaching hundreds of participants, we have received very positive feedback. Students really benefit from hands-on experience that is based on their own collective network/security suite. It is a chance for them to solve practical challenges and learn how to use all of the resources available to them, rather than a small subset of tools/knowledge. The scenarios are based on real world incidents that they may experience first hand, or might read about in things like breach reports or networking articles. In large and complex networks, operators need to understand how their systems work together, and training based on realistic scenarios helps with that
Lessons Learned
Prior to these events we were all experienced with the systems that the students were working with, and we knew what we wish we had been taught when we first began working with these tools. None of us had extensive experience providing training and we most of the issues we did encounter were process related. After providing multiple courses, we were able to adapt. Some examples of lessons learned:
- Automate wherever possible: As the white cell, our focus has to be on quickly generating activity so that we can focus on training the students. Setup and resetting of sensors, account provisioning, and attack execution need to be automated to the greatest extent possible.
- Organization is the key to a good day: We created networks using a large virtualized network, which meant that we were using many different systems to execute things. Every single document, signature, or test file that you need has to be quickly accessible. You will waste a lot of time rewriting or searching for things if they are scattered in some unknown place.
- Be prepared to Adapt: Attacks and networks are always changing, and so should the course. Implement new scenarios and techniques regularly to keep challenging the students. Keep an eye on security news to learn about new attacks. An abundance of open source content being developed by the community can be used to spin up new systems and challenges for the participants.
As a participant, it can be difficult to learn how to work with a large suite of networking and security tools. Providing people with hands-on training based on real world examples is a way for them to learn how to work with all of the tools collectively, rather than individually. From our experiences, we found that students enjoy learning through these scenarios more than lectures for vendor/product specific training. They have the opportunity to solve challenges using all of the resources available to them. Through our scenarios, we are also able to challenge students using attacks that are based on things like recent breaches or attack techniques from the security industry. Scenario-Based Training is a great approach to teach your network engineers and security analysts how to work in their own turf and learn how to resolve incidents.
Related Articles
Delivering More Agility, More Portability through Powerful Compact Solutions
For the first time, SealingTech exhibited at the AUSA Global Force Symposium & Exposition in Huntsville, Alabama. With a large number of Huntsville natives in attendance, it provided a good…
Harnessing AI for the Cyber Warfighter
When deploying junior and senior cyber operators on a mission, experience levels amongst the team will vary. At times, junior operators may have questions and need to interact with unfamiliar…
SealingTech and Parsons: Rocky Mountain Cyberspace Symposium 2025
In February, the SealingTech team attended Rocky Mountain Cyberspace Symposium (RMCS) in Colorado Springs, Colorado. This year’s theme focused on “Securing the Future: Cyber Capabilities, All-Domain Superiority, and Strategic Advantage.” …
Could your news use a jolt?
Find out what’s happening across the cyber landscape every month with The Lightning Report.
Be privy to the latest trends and evolutions, along with strategies to safeguard your government agency or enterprise from cyber threats. Subscribe now.